More and more companies use S/MIME eMail signatures in Outlook to make mail traffic more authentic. (And this is not only because of the effectiveness of GDPR.)
I am also a big fan of using security mechanisms like S/MIME. Actually, security and usability are not the best friends yet as we know. This led to a problem which came up last year:
At the beginning of 2018 a new vulnerability was discovered. It exploits the advantages of S/MIME in combination with Microsoft Outlook. The attack was published as EFAIL.
What the hell is EFAIL?
The EFAIL attack affects emails encrypted with the S/MIME (or PGP, including OpenPGP & GPG) protocols. When successfully executed the attacker is able to read targeted emails without obtaining the private key used to encrypt them.
It appends malicious HTML tags to an encrypted email and hopes the email client will unsafely parse that HTML.
What does EFAIL and the Topic of this blog have in common?
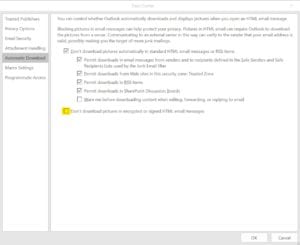
Microsoft added a security setting to the TrustCenter via the October Patchday. This setting is a simply way to reduce the risk to become a victim of the EFAIL attack – but it comes differently: The result was, that images and other external content in signed or encrypted messages cannot be loaded anymore: signed Newsletters for example had no pictures and lost their design.
How can I solve this problem?
Again, usability and security have not become friends yet. 🙂
But there is a quick way how you can solve this problem. Simply adjust the newly added setting in Outlook TrustCenter and uncheck the box “Don’t download pictures in encrypted or signed HTML email messages.“. Check out the following screenshot to find the setting.
Have you already had the experience? I am looking forward to a lively exchange in the comments!